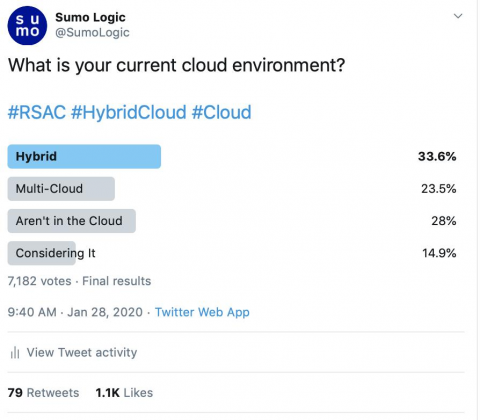
Google's New 'Badge of Shame' for Slow Websites
Google recently announced a new ‘Badge of Shame’ for slow websites in Chrome to improve user experience. We explain what this new badge means for websites and provide some tips to help you speed up your site.