How to Secure Your Data With Serverless Access Points
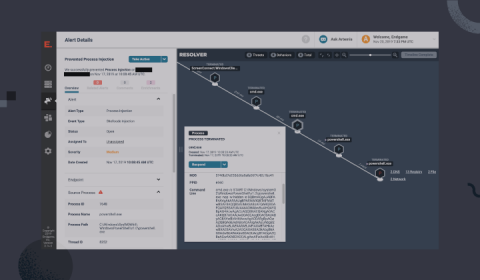
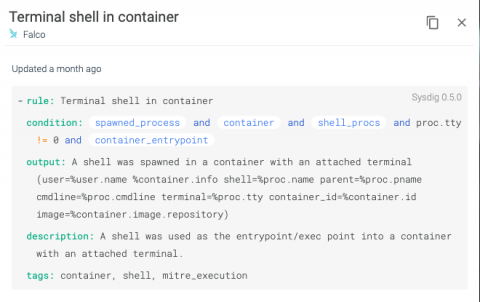
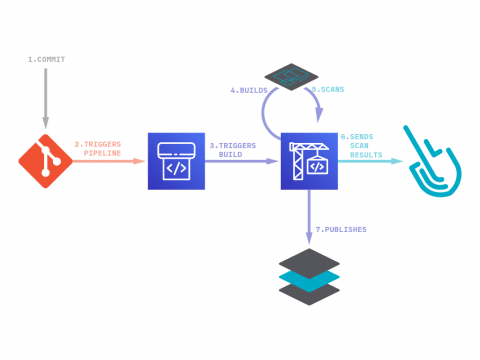
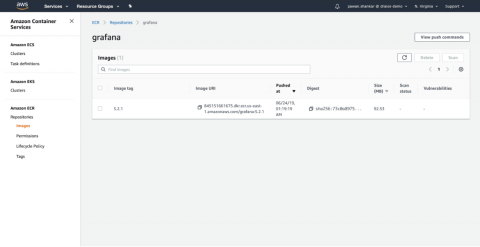
As our application scales and many services are accessing a multitude of data points for each workload needed, it is difficult to ensure each part of the system has the right set of data access permissions. In today’s world, one of the worse nightmares of a software business is data leaking and data privacy issues. Not only it affects the brand reputation, but could also expose the company to heavy fines and other regulatory sanctions.