Operations | Monitoring | ITSM | DevOps | Cloud
Risk Management
Five Hidden Security Risks You May Find with Traditional Backup Mechanisms
It’s always been important for managed services providers (MSPs) to exercise backup best practices but this has become even more important with the pandemic having reset employees’ expectations around remote work. Up to 74% of professionals believe that remote work is here to stay according to Growmotely, while 16% of companies globally are already completely remote and 40% offer hybrid working.
Gain visibility into manufacturing OT assets to reduce cyber risk
As manufacturing operational technology (OT) ecosystems grow more connected and complex, they become vulnerable to cyberattacks. In fact, the manufacturing sector was the most attacked industry in the world in 2021, according to IBM’s X-Force Threat Intelligence Index 2022. Manufacturing surpassed finance and insurance in the number of cyberattacks for the first time in five years. A large part of the industry’s vulnerability is due to a lack of visibility.
Internal Social Media Platforms and Risk Management
How a telecom company elevated integrated risk management and security
Managing risk and compliance in telecommunications is no easy feat. When a telecom company operates in underserved remote and rural communities—including hurricane-prone island markets and mountainous regions in the southwestern US—it can be even trickier. That’s where communications services company ATN International, based in Massachusetts, found itself. The company wanted a platform to elevate its integrated risk management (IRM) program.
Taming the supply chain: Addressing vendor risks to the nth tier
Vendor risk ranks alongside cybersecurity, compliance, reputational, and financial risks as one of the top risks to any organization. With any risk, you need to identify, monitor, and mitigate that risk, especially when it comes to your supply chain. The question for someone in my role as a senior manager of compliance management is: What level of risk is being posed and why? Stated another way: Do I really know what my supply chain is doing?
Rediscover ServiceNow Risk and Resilience
Forrester says ServiceNow is a Leader in third-party risk management
No matter what business or industry you’re in, you want your business partners to deliver. Sometimes what we get is unexpected: toxic ingredients, software bugs, data breaches, sketchy hiring practices, unvetted subcontractors. As hundreds and even thousands of third and fourth parties become more integral to business, your risk posture and success trajectory are heavily influenced by your partners’ business practices. That’s why you need automated third-party risk management.
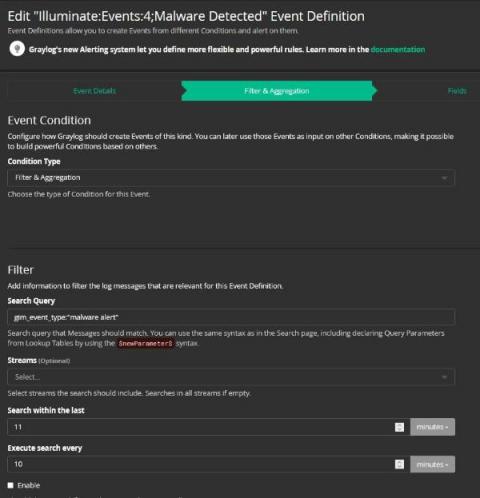
Cybersecurity Risk Management: Introduction to Security Analytics
It’s mid-morning. You’re scanning the daily news while enjoying a coffee break. You come across yet another headline broadcasting a supply chain data breach. Your heart skips a quick, almost undetectable, beat. You have the technology in the headline in your stack. You set aside your coffee and begin furiously scanning through the overwhelming number of alerts triggered across all your technologies.