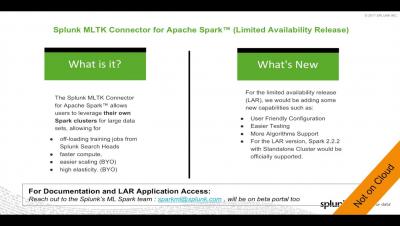
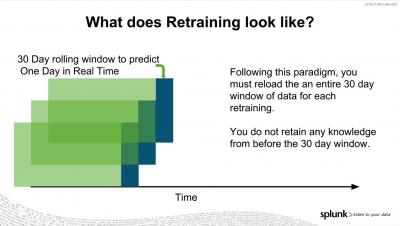
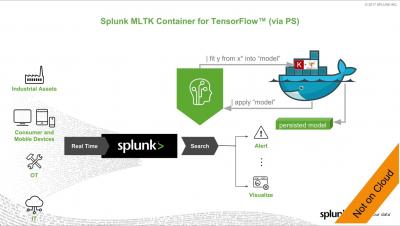
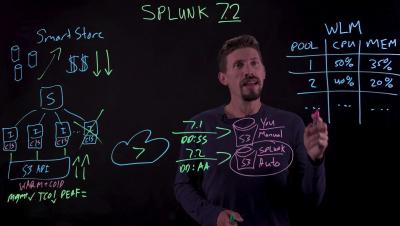
Top 3 AWS Lambda Performance Monitoring Tools
Serverless is often described as the abstraction to end all abstractions. VMs and standalone containers pale in comparison stateless functions. That pristine distinction between the application’s code and its stateful data is something we all dream of. Scalability, observability and high availability can now be realized on a global scale.