Operations | Monitoring | ITSM | DevOps | Cloud
ManageEngine
Simplifying security auditing, Part 3: Keeping insider threats in check
Insider threats are on the rise. In fact, both administrators and average employees are among the biggest security threats in an organization. When it comes to security auditing, there are two areas you need to focus on: Active Directory changes and individual user activity, particularly administrator activity.
Simplifying security auditing, Part 2: Auditing systems that store sensitive data
In part 1, we looked at an overview of auditing servers. In this blog, we’ll discuss which events you need to audit in your databases and file servers where sensitive data is stored. New data protection regulations and large-scale global attacks have made this more important than ever before. The main goal is to not only ensure that the accesses and modifications to sensitive data in your network are authorized, but also that file and column integrity are maintained.
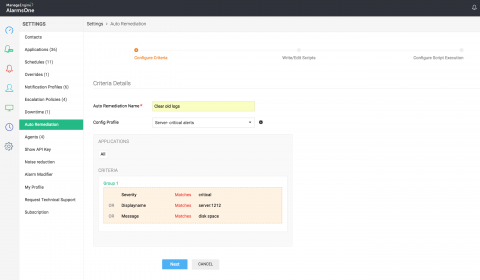
Auto-remediate your IT incidents using scripts
It’s 2am. You receive a notification from your monitoring tool. A host server ran out of space and your system is down. Now you need to get out of bed and clear the log files of whatever service has filled up your available disk space. Ugh. Now, imagine that an automated action is triggered, the log files are cleared, and your system is up and running again without requiring a single thing from you. Sounds cool, right?
Simplifying security auditing, Part 1: Regularly reviewing server activity
Everyone knows about the importance of log management in IT security. Yet, organizations struggle with implementing effective log management techniques in their networks. This blog series aims to revisit the fundamentals of log management and discuss the different security events you need to keep track of in each of the different systems in your environment.
Less is more: Role-based performance monitoring with OpManager
Much of a business’ strength lies in its network infrastructure. One way to keep your business up and running is by proactively monitoring key network performance indicators. However, with a plethora of parameters to keep an eye on, and a lot of data to skim through, there’s only so much an IT professional can do while troubleshooting. This is a common challenge many IT teams in the network infrastructure monitoring field face, and it often increases the time taken to resolve issues.
Integrate OpManager with AlarmsOne and manage your alerts like a pro
OpManager helps enterprises monitor their network, devices, servers, firewall, and more. While all this helps keep your systems up and running at all times, effectively managing alerts is another challenge altogether. If you’re using a number of IT management tools, it can be hard to address issues like alert noise, inflexible on-call scheduling, and escalations.
The top 5 VM metrics that every Azure admin should monitor
The age-old approach of storing data on self-hosted data centers is rapidly becoming obsolete, with most organizations shifting towards cloud solutions like Microsoft Azure. Azure delivers more than 600 services like on-demand computing, storage, data management, and networking, and virtual machines (VMs) are an important component of the Azure cloud platform.
How to leverage SIEM to meet the GDPR's requirements
Today’s businesses run on data. From getting customer information for payment, processing employee information for payroll, using publicly available data for targeted advertising, to tracking people’s behavior for marketing, data has become the power center of organizations. But with this increased emphasis on data, organizations are now burdened with greater responsibilities.
Five worthy reads: Top-notch customer service with chatbots
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore how chatbots decode the mysteries of customer engagement.