Monitoring MS SQL Server with Applications Manager
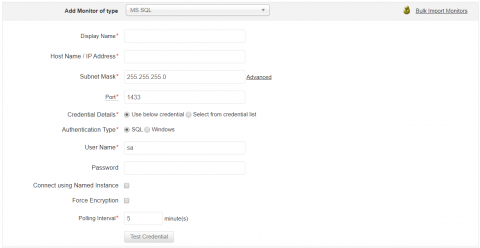
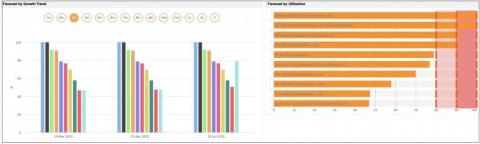
MS SQL, Microsoft’s relational database management system (RDBMS), is known for its broad spectrum of capabilities such as transaction processing, business intelligence, and analytics. This is why most businesses trust and invest in SQL for their data storage and access needs. What are the benefits of monitoring SQL servers? Applications Manager offers proactive SQL server monitoring.