Work from home series, part 1: Remote authentication and password management
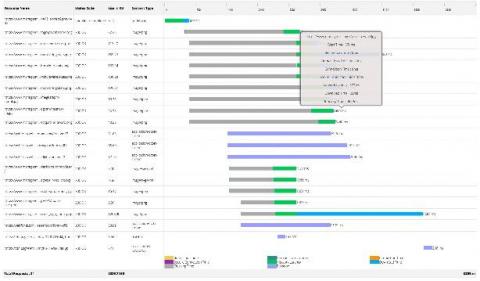
One of the primary concerns of IT admins when employees start working remotely is authenticating users. How can employees securely log in to their accounts while working remotely? What happens if users get locked out of their accounts? These are some of the questions that organizations are asking themselves when implementing work-from-home policies.