Operations | Monitoring | ITSM | DevOps | Cloud
Automation
4 Smart Automation Systems to Improve Your Warehouse Business
The 7 IT Automations for Highly Effective Organization: IT incident Remediation | Low Disk Space
DevOps Cheat Sheet: Deployment Automation
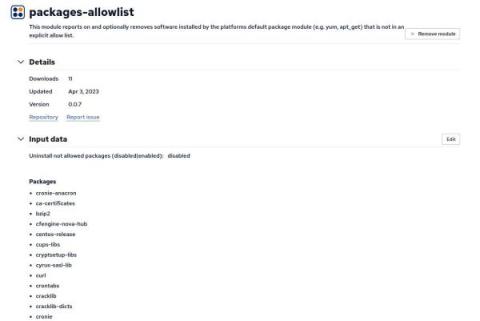
Improved software compliance with packages-allowlist
Having a list of software that is allowed to be installed on a host is a strategy to prevent and fix security gaps and maintain compliance with operational guidelines. This zero-trust methodology ensures that only explicitly permitted applications are allowed to be present on a host unlike package block-listing which enumerates an explicit list of software that is not allowed to be present. In fact, with a software allow-list, you are essentially block-listing everything except the software you allow.
Runbook Automation | What It Is & How To Do It
Why Network Automation Is an I&O Imperative
While network automation tools can help infrastructure and operations (I&O) teams improve their agility, lower their costs, and reduce the risk of manual errors, network management stubbornly remains a largely manual process. According to a recent Gartner report, less than 35% of enterprise network activities are automated today, forcing enterprises to run largely using a ClickOps model.
MSP Automation: Transform & Scale your MSP Business
MSP Automation was the main focus of our recent webinar, which covered how Managed Service Providers can transform the scalability of their businesses by removing the headaches of manual request processing. The webinar was widely attended by enterprise IT staff too , particularly those with an ethos of delivering an experience (rather than a service level). The same principles apply, so here’s an overview of what was covered during the session.