Operations | Monitoring | ITSM | DevOps | Cloud
Technology
The latest News and Information on APIs, Mobile, AI, Machine Learning, IoT, Open Source and more!
Embedded Linux for teams
A Linux kernel for each developer team, which uses it to bring up target boards. Bespoke, built, issued, and maintained over years by the vendor. Teams that focus on building great apps, rather than figuring out hardware dependencies. Happy developers that bootstrap smart devices in no time. This is what highly productive embedded systems development should look like. Let’s unpack that vision.
Finding the Bug in the Haystack with Machine Learning: Logz.io Exceptions in Kibana
Logz.io is releasing its AI-powered Exceptions, a revamped version of our Application Insights, fully embedded in your Kibana Discover experience, to boost your troubleshooting experience and help you find bugs in the log haystack.
JFrog Support Providing Next Level Artificial Intelligence (AI) Experience
Multi-cloud AI/ML and DevSecOps on Kubernetes
Learn more about AI/ML: https://ubuntu.com/kubeflow
Get Kubernetes on Ubuntu: https://ubuntu.com/kubernetes
In collaboration with: https://www.metrostarsystems.com/
Mattermost integrations: Sending and receiving data with the Mattermost API
In the first three installments in this series, you learned how to send and request data with outgoing webhooks, incoming webhooks, and slash commands. In this article, you learn how to do this with the Mattermost API. Setting up webhooks or slash commands in Mattermost is very easy. Using the Mattermost API requires a few more steps. At the same time, the API is way more versatile and powerful than the other methods. Once you have made your first connection to the API, you will love it!
Cybersecurity defenses for IIoT
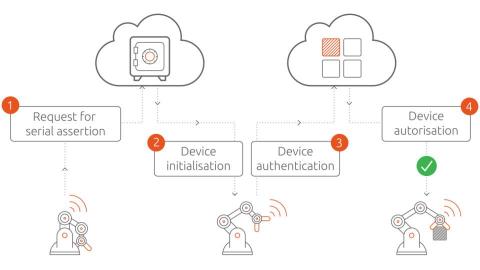
Cybersecurity attacks on industrial IoT solutions can have detrimental consequences. This is the case because IoT devices record privacy-sensitive data and control production assets. Therefore, demonstrable trustworthiness is prerequisite to IoT adoption in industrial settings. Fortunately, IT security is a mature field. Experts have identified classes of threats devices may be subject to. Let’s discuss these threat patterns and mitigation strategies in the IIoT context.
Percepio DevAlert - IoT Device Monitoring and Diagnostics (very short summary)
Kubernetes Is Not Just Kubernetes-Ramp Up with These Eight Open Source Projects
Microservices vs API
In this article, we’ll cover the key differences between APIs and microservices as answered by our contributors consisting of senior decision-makers and CTOs from technology companies around the world. One of the most popular ways to consume data from a web service is through a web application programming interface (API). By interface, we are referring to an agreement, or schema, that anyone using this API must abide by.