Operations | Monitoring | ITSM | DevOps | Cloud
Cloud
The latest News and Information on Cloud monitoring, security and related technologies.
Getting Started With Azure Database for PostgreSQL
Automate AWS Lambda function deployments to AWS CDK
When you build a cloud-based application, you can choose to deploy the resources using the GUI (Graphical User Interface) or CLI (Command Line Interface) provided by the cloud provider. This approach can work well with just a handful of resources, but as the complexity of your application increases, it can become difficult to manage the infrastructure manually.
AWS Monitoring Tool
How to retrieve Azure Key Vault Secrets using Azure Functions (Part II)
How Cloud Network Monitoring Is Critical To Business Success
A rising number of businesses are adopting and utilizing cloud services and capabilities with remarkable success. But embracing cloud tools and services often brings unexpected changes for business leaders and IT teams, especially because of the way in which cloud adoption has altered how networks are monitored and managed.
AppDynamics Cloud: Kubernetes Overview
Intelligent Instance Selection for Your Kubernetes Workloads
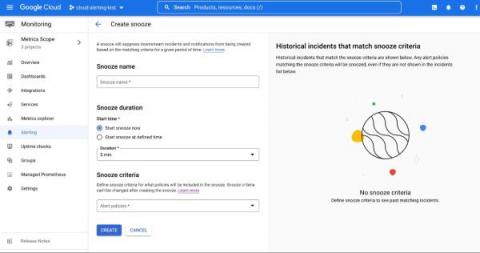
Snooze your alert policies in Cloud Monitoring
Does your development team want to snooze alerts during non-business hours? Or proactively prevent the creation of expected alerts for an upcoming expected maintenance window? Cloud Alerting in Google's Cloud operations suite now supports the ability to snooze alert policies for a given period of time. You can create a Snooze by providing specific alert policies and a time period. During this window, if the alert policy is violated, no incidents or notifications are created.
Seven Tools to Help You Become a Better Serverless Developer
Serverless technologies let us do more with less effort, time and energy. They let us focus on creating user value and let the cloud handle undifferentiated heavy-lifting like scaling and securing the underlying infrastructure that runs our code. Serverless technologies have allowed me to accomplish tasks as a solo engineer that used to take a whole team of engineers to accomplish, and I’m able to complete these tasks in a fraction of the time and cost to my customers.