Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
Best Site Builders for Linux
The importance of behavior analytics in your organization's cybersecurity
Collin’s dictionary defines “behavior pattern” as a recurrent way of acting by an individual or group toward a given object or in a given situation. Analyzing and understanding the behavior patterns of individuals has proven to provide in-depth solutions to problems in different walks of life, including cybersecurity.
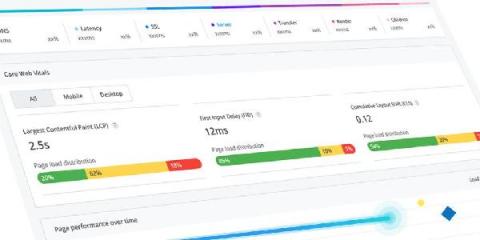
Introducing native support for Core Web Vitals
In December last year, we released tracking for Core Web Vitals using custom tagging so that you can have consolidated performance metrics that accurately reflect your customer's digital experience. Today, we are excited to continue this journey and announce our native first-class support for Core Web Vitals (CWV) tracking within Real User Monitoring. Now, you can see a detailed overview of how your website performs against Google's modern user-centric metrics, alongside all the diagnostics you need to take action.
Our first community update - Signal #01
Excited to launch our first newsletter. We are delighted to have crossed 1.6k stars on GitHub, growing more than 30% last month. Catch up on what we're upto at SigNoz!
Uptime Monitoring: A One-week Project, a Decade In the Making
We recently released uptime monitoring, a pretty big addition to our set of features. Our customers have often requested it, and it was a logical next step for us to add uptime monitoring to our app. In today’s post, we’ll explain how we went from considering uptime monitoring impossible to build, to building it in a week. We’ll break down how seemingly over-engineering can really pay off in the end.
Investigating Network Anomalies - A sample workflow
Network anomalies vary in nature. While some of them are easy to understand at first sight, there are anomalies that require investigation before a resolution can be made. The MITRE ATT&CK framework introduced in Kemp Flowmon ADS 11.3 streamlines the analysis process and gives security analyst additional insight by leveraging knowledge of adversaries' techniques explaining network anomalies via the ATT&CK framework point of view.
Event-driven autoscaling in Kubernetes
In modern cloud architecture applications are broken down into independent building blocks usually as microservices. These microservices allow teams to be more agile and deploy faster. Microservices form distributed systems in which communication between them is critical in order to create the unified system. A good practice for such communication is to implement an event-driven architecture.
HTC Automates Network Operations, Fueling Data-Driven Decision-Making During Emergencies
Severe weather in South Carolina comes with the territory, and for a local communications service provider like HTC, that translates to service outages for the internet, streaming video, phone, and wireless networks it provides to predominantly rural communities. When these events strike, the Emergency Operations Center (EOC) at HTC faces enormous pressure not only to maintain services, but to prioritize customer support efforts and restore services as quickly as possible.
Ensuring compliance with DISA STIGs, NIST 800-53, CMMC, and RMF
This blog is the second in a four-part series on infrastructure automation for government agencies that are modernizing digital systems while grappling with budget and staffing constraints and the challenges of COVID-19.