Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
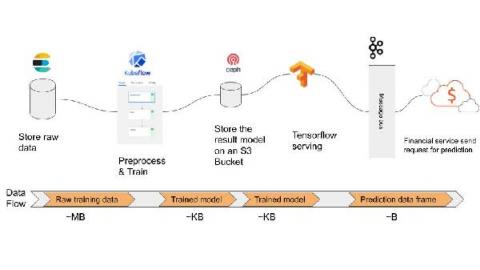
AI on premise: benefits and a predictive-modeling use case
Running an Artificial Intelligence (AI) infrastructure on premise has major challenges like high capex and requires internal expertise. It can provide a lot of benefits for organisations that want to establish an AI strategy. The solution outlined in this post illustrates the power and the utility of the universal Operator Lifecycle Manager (OLM) using Juju, a universal OLM, to create and manage on premise AI infrastructure.
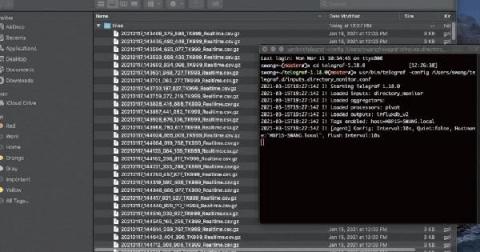
New in Telegraf 1.18.0: Beat, Directory, NFS, XML, Sensu, SignalFX and More!
Last week we released Telegraf 1.18 with a range of new plugins including Elastic Beats, directory monitoring, NFS, XML parsing and some aggregators and processors to help with your data ingestion. All of these packages were written in Go 1.16.2. This was one of our largest releases in a while and couldn’t have been done without the 70+ Telegraf community members who contributed to writing plugins, fixing bugs, reviewing code, and everything else to improve Telegraf!
Monitoring Logs for Insider Threats During Turbulent Times
For logs and tracking insider threats, you need to start with the relevant data. In these turbulent times, IT teams leverage centralized log management solutions for making decisions. As the challenges change, the way you’re monitoring logs for insider threats needs to change too. Furloughs, workforce reductions, and business practice changes as part of the COVID stay-at-home mandates impacted IT teams.
What is the difference between Database, Data Warehouse, and Data Lake?
Data is everywhere in the form of values, text, numbers, pictures and so on that can be stored and used anytime when required. The importance of data and data storage systems has gained recognition since businesses find the potential of big data and its use cases. The data was with us always, but the possibilities to use it effectively were an arduous task.
Human-centered IT service management: The next great differentiator
Positive employee and customer experiences are critical to business growth and digital transformation success. But, such experiences require revamping how organizations structure, deliver, and measure IT services. That’s why human-centered IT service management is growing in popularity for companies that want to innovate IT and gain a competitive advantage. Here are some insights for IT leaders who may be hesitant to take the leap into human-centered ITSM.
Unraveling open port threats and enhancing security with port scanning tools
From exposing your network vulnerabilities to becoming a passageway for intruders, open ports can pose several risk vectors that threaten your network’s confidentiality, integrity, and availability. This is why it’s a best practice to close your open ports. To tackle the risks introduced by open ports, network admins rely on port scanning tools to identify, inspect, analyze, and close open ports in their networks.
SolarWinds Head Geeks to Discuss "Next Normal" Network Improvements Needed at Cisco Live! 2021
Core Web Vitals: Google's Upcoming Ranking Changes
From 1st May 2021, Google will start judging your website based on a new set of performance metrics called Core Web Vitals. This initiative is focused around user experience and will become part of Google’s ranking algorithm. Failing them is bad, getting them right is a huge opportunity. Only 23% of businesses currently pass these tests consistently, so organic SEO will be negatively impacted for the large majority of companies.
10 Best Tools for Monitoring Wireless Access Points
Monitoring wireless access points is business-critical, allowing teams to facilitate day-to-day workflows. These wireless access points (APs or WAPs) provide strong Wi-Fi signals and transmission ranges for sending and receiving valued information. But wireless access points are susceptible to cyberattacks that jeopardize your revenue and reputation.