Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
Enabling Secure Access for the Federal Government - Meeting Comply to Connect Mandates
Government IT organizations must demonstrate and maintain compliance with a large and growing number of regulations and standards around network access control (NAC), ensuring that all connected devices to their environment are not vulnerable is a key requirement. Comply to connect (C2C) simplifies this by enforcing that patches and hardened configurations are applied to devices before they connect and updated continually.
11 DevOps Metrics To Monitor for Organizational Success
How to Deploy a Kubernetes Cluster on AWS
If your organization is planning to use AWS for deploying new releases, the deployment process can be tricky for teams outside of operations to learn and use, especially for those who don’t have expertise in the tooling to automate deployment. And, because there are several ways to deploy Kubernetes on AWS, including Amazon’s own EKS, understanding the different deployment options can be tough to navigate.
Guidelines for picking where to send monitoring alerts
If you've ever had to be on the receiving end of a monitoring system that uses email for alerts, you know how noisy things can get. Particularly if you're working in an agency or freelance-like environment, with dozens of client sites to maintain. You get so many emails that you start looking into integrations with third-party services like Zapier, and coming up with more and more complex rules to try reduce the noise.
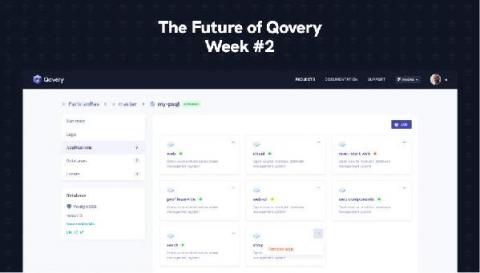
The Future of Qovery - Week #2
During the next nine weeks, our team will work to improve the overall experience of Qovery. We gathered all your feedback (thank you to our wonderful community 🙏), and we decided to make significant changes to make Qovery a better place to deploy and manage your apps. This series will reveal all the changes and features you will get in the next major release of Qovery. Let's go!
What if You Could Autonomously Monitor Across Your Databases?
When DevOps teams talk about monitoring a database, the primary motivation is to ensure that the database won’t suffer a performance hiccup. Long queries, timeouts and table scans are among the most popular causes behind lousy customer experience. However, in recent years, more data has been shifted to cloud databases.
Predictive Analytics Use Cases In The Retail Industry
In an expanded and commercial industry space new and innovative opportunities are presented to retail organizations from several novel sources of data, log files, and from transaction information to sensor data to achieve unmatched value and combative advantage in their respective fields. In order to attain customer satisfaction and to flourish their business, people across the organization must be empowered, so that swift and accurate decisions can be attained.
Five worthy reads: Understanding quantum computing and its impact on cybersecurity
Five worthy reads is a regular column on five noteworthy items we discovered while researching trending and timeless topics. In this week’s edition, let’s explore how quantum computing works and how it impacts cybersecurity.
Logback Configuration Example: Tutorial on How to Use It for Logging in Java
Troubleshooting issues in your applications can be a complicated task requiring visibility into various components. In the worst-case scenario, to understand what is happening and why it is happening you will need metrics, logs, and traces combined together. Having that information will give you the possibility to slice and dice the data and get to the root cause efficiently. In this article, we will focus on logs and how to configure logging for your Java applications.