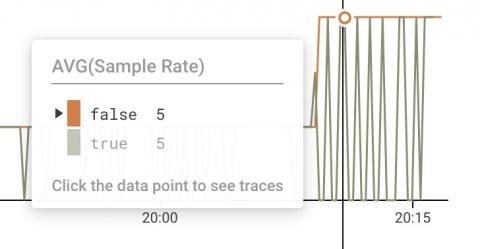
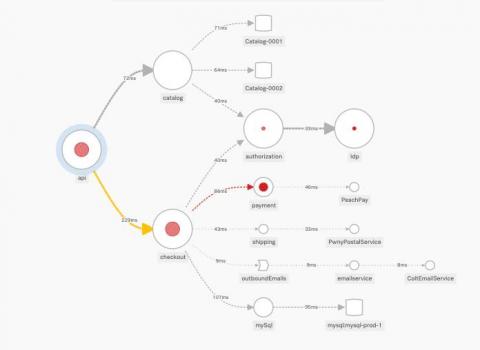
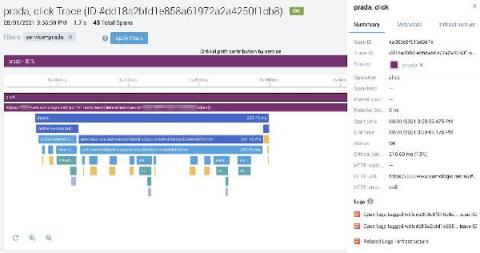
How to Successfully Deploy Kubernetes Across Multi-Cloud Environments
Today’s enterprise organizations are using some form of multi-cloud infrastructure, and the numbers don’t lie. According to Flexera’s 2020 State of the Cloud report, an average of 2.2 public clouds are being used per enterprise company. And in a different report from the Everest Group, 58% of enterprise workloads are on hybrid or private cloud. The sheer increase in multi-cloud usage illustrates it’s growing popularity across enterprises.