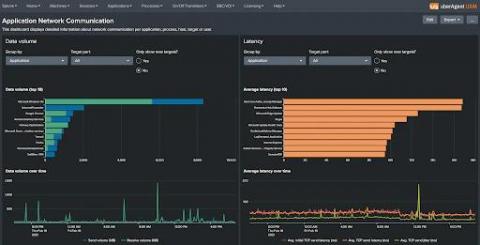
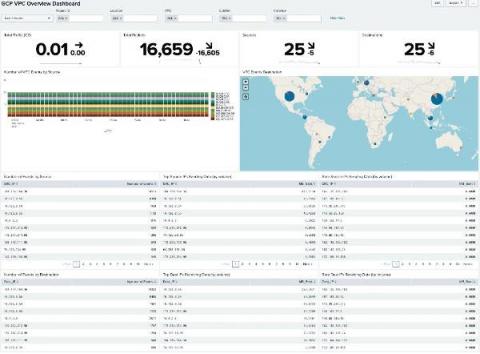
Enriching Splunk Contact Center Analytics with uberAgent Endpoint Monitoring
Like many other industries, contact centers are increasingly relying on employees working from home. The WFH trend poses new challenges, but it also surfaces issues that were largely ignored before. This article explains how holistic monitoring with Splunk Contact Center Analytics and uberAgent help drive exceptional customer service.