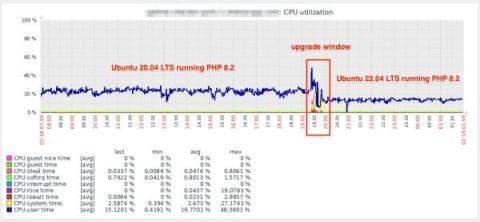
Reducing PHP's CPU usage by nearly 40% by upgrading from Ubuntu 20.04 to 22.04
Over these past few weeks, we've updated our Ubuntu 20.04 LTS uptime servers to Ubuntu 22.04 LTS. The reason was mostly just staying up-to-date, but we had a surprising side-effect that was unexpected but very welcome.