Using Ivanti Neurons and MobileIron UEM to Handle the Latest iOS, iPadOS, and tvOS Vulnerabilities Proactively
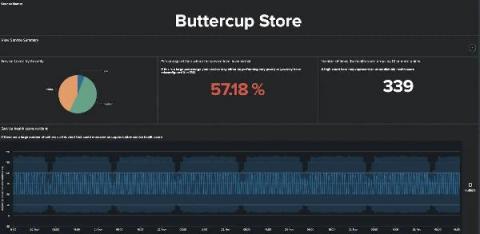
On Tuesday, January 26, 2021, Apple released version 14.4 of its iOS, iPadOS, and tvOS products that included patches for three security vulnerabilities that affect iPhone 6s and later, iPad Air 2 and later, iPad mini 4 and later, and iPod touch 7th generation, as well as Apple TV.