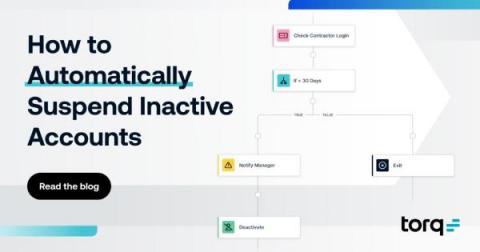
An Introduction to Windows Event Logs
The value of log files goes far beyond their traditional remit of diagnosing and troubleshooting issues reported in production. They provide a wealth of information about your systems’ health and behavior, helping you spot issues as they emerge. By aggregating and analyzing your log file data in real time, you can proactively monitor your network, servers, user workstations, and applications for signs of trouble.