How to audit Node.js modules
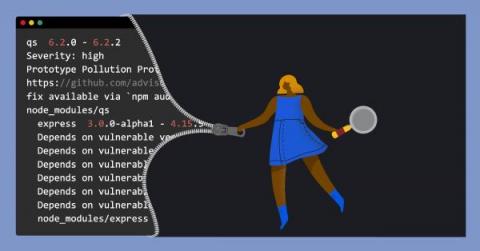
Node.js is one of the best and most widely used Javascript runtimes used for building APIs. But, this popularity status has led to many hackers distributing insecure modules that exploit the Node.js application or provide a weak point for exploitation. In this tutorial, you will learn how to audit Node.js modules and also detect vulnerabilities in modules using npm audit.