Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
What is Zero-Trust? How can it be a game-changer for the security, control, and monitoring of your IT infrastructure?
Imagining the Future of Engineering: Insights from top women in tech
APM Vision for Open Source and Security
Earlier this month, we shared exciting news with our first placement in the 2022 Gartner® Magic Quadrant™ for Application Performance Monitoring and Observability: we are in the Visionary Quadrant. This research is near to my heart, as I led this research for four years; so, I wanted to reflect on why this is an accurate placement for Logz.io. The Visionary Quadrant is designated for those organizations who are pushing the boundaries of a specific market and technology.
Delivering Outcome-Based Results at Gartner's Security & Risk Summit
It’s common for most CISOs to lead off a security conversation by comparing what other companies in the industry are spending on cybersecurity and simply matching that. After all, regardless of the results, the CISO can always tell the board of directors they’re following industry guidelines around security budgets. The problem is security outcomes are bad regardless of budgets. It’s not what you spend. It’s the results you get that matter.
Accelerating the Path to Managed Cybersecurity with M&A
MSPs operate in a challenging and competitive marketplace. Small and medium-sized business (SMB) customers increasingly view the core IT infrastructure support services MSPs have long provided as commodities. At the same time, competitors are growing larger and more sophisticated as industry consolidation continues. Private equity investments have created more than 80 MSP platforms that are aggressively pursuing add-on acquisition opportunities.
Cove Data Protection Modernizes Disaster Recovery as-a-Service with New Standby Image Feature
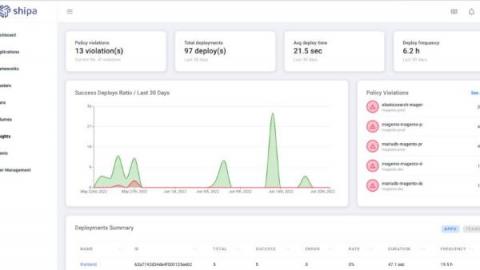
Are your applications secure? Can you find it out without complex rules?
The modernization of infrastructure and applications is driving the rapid growth of containers, and as companies scale the adoption of Kubernetes, it’s critical to incorporate security and compliance. The challenge? Compliance and security is a journey, not a state in time, and application security in Kubernetes has a large surface area. This challenge increases exponentially as you run more applications, onboard more developers, add more environments, add new pipelines, and more.
How To Identify and Stop a Phishing Attack
Cribl.Cloud: Are You Ready to Fly Solo?
Many years ago, I attained my private pilot’s license. This entailed completing a very structured program, similar to how most companies introduce a product to a new user. Let’s be honest, there is a really good reason for this – to avoid the crash and burn. With flight training, it’s literal, while with products it’s a bit more figurative (except when you YOLO something into production–that can cause a crash and burn–and leave for a bad first impression).