Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
How to Easily perform Data Masking of Social Security Numbers (SSNs) in Log files or Events in 4 Ways using Data Bots
How Puppet provides cyber security resilience to customers
You only have to read regular news reports about the multiple outages across household names in banking and financial services, resulting in customers being unable to access their bank accounts, to know that cyber security resilience has never been more important and is on every organization’s radar. The threat of regulatory action, heavy fines, and the potential loss of banking licenses is very real.
New report: Ransomware continues to rise. Here's how to get ahead of it.
Ransomware experienced a stunning surge in prevalence and sophistication throughout the pandemic. Threat actors capitalized on a frequently shaky transition to a remote, digital business landscape. With so many businesses prioritizing basic functionality over proactive security, vulnerabilities have been unprecedented – and very much exploited.
CIS-Harden your Ubuntu in Google Cloud
CIS Benchmarks are best practices for the secure configuration of a target system. The Center for Internet Security, Inc. (CIS®) is the authority backing CIS Benchmarks. Ubuntu Pro is entitled to be CIS compliant and packaged with CIS toolings from Canonical. Let’s SSH into your Ubuntu Pro virtual machine. If you haven’t yet upgrade your Ubuntu LTS to Ubuntu Pro, please follow this tutorial.
History of Open Source Identity Management (part 1)
Few computing concepts are as ubiquitous as identity and access management. There isn’t a single day that goes by without us being asked for credentials, passwords or pin codes. Yet very few know the origins and the evolution of the technologies behind them. This is the first of two blog posts where we will look at the history of open-source identity management. We will cover the main open-source protocols and standards that shaped it, from its origins to the modern days.
How to Optimize Your Cyber Security and Performance Monitoring Tools Using Load Balancing
The capacity to scale and process high data traffic by monitoring appliances is a critical requirement for organizations aiming to enhance or improve their security and protection from external threats. Excessive incoming traffic demands high-monitoring capabilities as it overwhelms the monitoring tools and places computational bounds that increase exponentially.
Monitoring network security with Aruba Clearpass, Grafana and Graphite
In this article, we will explore why it is imperative to constantly monitor network security metrics, what Aruba Clearpass is, and how it helps us manage network security. Then we will look at what Graphite and Grafana are and how to analyze metrics with their help. Finally, we will learn how MetricFire can make it easier for us to work with Graphite and Grafana.
Three countries, outside the European Community, that are reforming their privacy policies
Are you not a little curious? Even a little bit, right under your chin or your temple about how they deal with privacy policies in other countries? Aren’t you? Well, surprise! Today, in Pandora FMS blog, we are going to get it out of our system by discussing how they do it, how they deal with the protection of international data and privacy, in at least three countries outside the European Community.
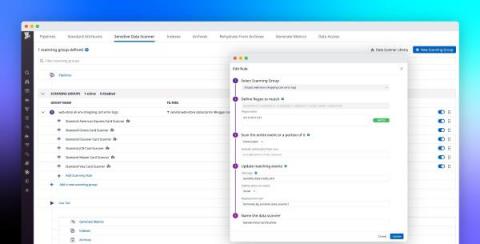
Build a modern data compliance strategy with Datadog's Sensitive Data Scanner
Within distributed applications, data moves across many loosely connected endpoints, microservices, and teams, making it difficult to know when services are storing—or inadvertently leaking—sensitive data. This is especially true for governance, risk management, and compliance (GRC) or other security teams working for enterprises in highly regulated industries, such as healthcare, banking, insurance, and financial services.