SOARing to the Clouds with Splunk SOAR
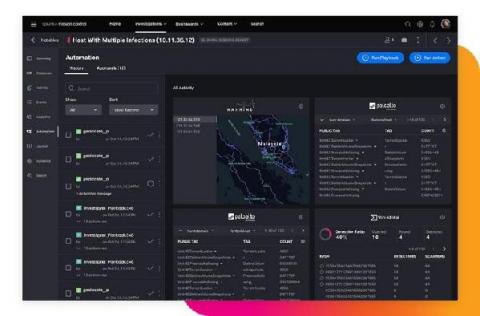
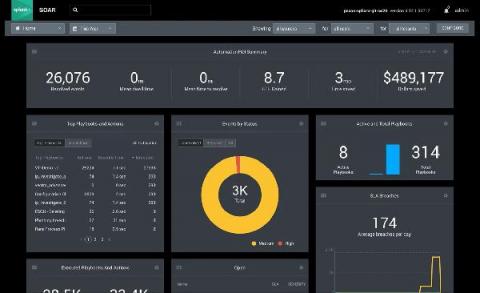
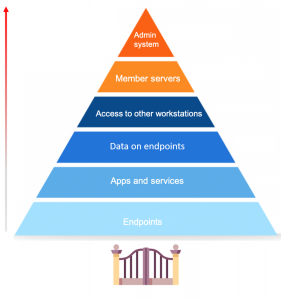
For years, security practitioners have kicked and screamed about their reality. There are too many alerts to fully investigate and manually resolve every day. There is a massive talent shortage of qualified security professionals across the globe. Then couple that with analyst burnout and siloed security point-products. All of these factors are preventing security operation centers (SOCs) from operating at their full potential, with increased efficiency, performance and speed.