Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
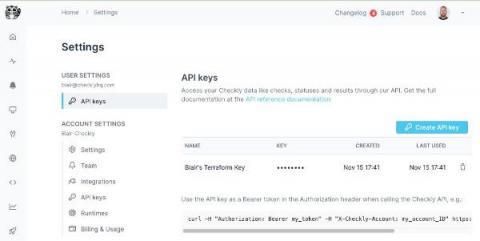
User-scoped API Keys
Checkly has released a change to the way API keys are created and managed. In the past, API keys were account-scoped. These account-scoped keys have full access rights to your Checkly account and no accountability to which user is using the key. When we originally built Checkly, we made it a tool to enable individual developers to quickly and easily set up browser and API checks. We help ensure your web applications are up and running and send alerts when something goes wrong.
A comprehensive lifecycle approach to ransomware defense
Ransomware continues to be a costly and growing problem. According to Infosecurity Magazine, the number of ransomware attacks grew 288% between the first and second quarters of 2021. Cybersecurity Ventures estimated a ransomware attack occurs every 11 seconds, Cybercrime Magazine reports. The resulting price tag from ransomware is truly staggering.
Understanding business and security risk
Even if an organization has developed a governance team, aligning integration decisions with business needs must be incorporated into the zero trust architecture. The company’s business model drives the applications chosen. The senior leadership team needs someone who can translate technology risks and apply them to business risks. For example, security might be an organization’s differentiator.
Controlled Unclassified Information: Top 4 Management Tips
How Puppet supports desktop and laptop automation in a changing world
The world has changed since I started out on a help desk in Colorado 25 years ago. In those long ago years, a company’s desktop machines actually lived under the desks of many in the organization (and often doubled as a foot warmer!) and configuration was done machine by machine manually, or maybe even by some script that was created to run at login if we were lucky. If there were laptops in use by the business users, they were a lot less mobile and rarer than in today’s business world...
ARTICA becomes official CNA
There are “good” hackers. They call themselves security analysts and some even devote their time to working for the common good. They investigate possible vulnerabilities in public and known applications, and when they find a possible security flaw that could endanger the users of those applications, they report that vulnerability to the software manufacturer. There is no reward, they are not paid for it, they do it to make the world safer.
3 Ways To Prevent Cyber Security Threats When Marketing Online
Why Google SSO is so important
We’ve all become more security conscious online with password protection being one of the biggest problems when it comes to potential malicious threats to our personal data. As we start using more and more websites and applications, the need to have unique passwords for each one becomes a goliath task.