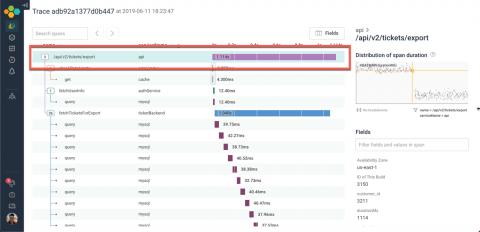
Features review from 2017
This is the second edition of our features review from the past few years, here we will share some features that were created or updated in 2017. We are currently moving content from our old blog platform so all features mentioned here are not new but it is always good to take a fresh look at things. And as we are always upgrading & enhancing features, some of the items have been edited to reflect the current state.