Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
SwampUP Leap: AppsFlyer Transforms Its Artifact Management with Artifactory's Single Source of Truth
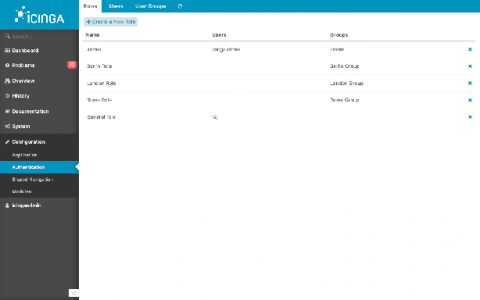
Icinga Web permissions and restrictions (how do they work, examples)
Permissions and restrictions are something used to control how much access is provided to a particular user or user group. Therefore one must first understand what is the role of a user or a group. Here, you will understand permissions and restrictions through configuring users, user groups and roles. They can either be created using configuration files or web interface. When the Icinga Web 2 is installed a default user with admin access is configured.
PagerDuty Paying Dividends for Form3's Digital Payment Platform
Your payment systems have slowed to a crawl, customers are getting impatient and abandoning their shopping carts both online and in stores, and you’re losing money every minute this problem goes on. Behind the scenes, technical responders are scrambling to resolve the issue before it impacts more customers—and before even more money is lost.
Tackling Financial Crime is a Matter of Data: Fresh Thinking on an Age-Old Problem
Financial firms need to take a holistic view on their financial crime defenses to keep pace with the changing crime landscape. Dealing with the onslaught of attacks has historically elicited a Pavlovian response to this age-old problem — increased regulations or tighter risk management protocols, which in turn have proven to be ineffective over the long term.
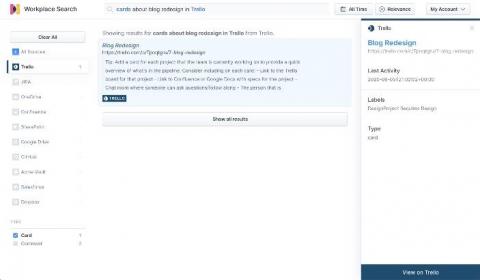
How to ingest data from Trello into Elastic Workplace Search
In our previous post, we introduced the concept of the Elastic Workplace Search Custom Source API as a means of adding data for which a prebuilt content source integration isn’t available. We used a simple example — a CSV file of contact information — to demonstrate the process along with the use of the associated REST API. In this post, we explore ingesting data from a more complex organizational source: Trello.
Tools to Manage Cyber Risk in a Growing Organization
Within the cyber security industry, it is well known that as a company grows, so does its attack surface. This trend lends itself largely to the fact that as more employees are hired, more company-owned machines (laptops, tablets, etc.) are distributed. The risk is that once a company-owned machine is given to an employee, it is up to the employee whether to follow the security best practices set forth by your company. Your technological asset has now become a security risk.
Crash Course on AWS CDK and Serverless with REST API and Data Lake Analytical Querying
This is a hands-on course on how to deploy a fully Serverless web app using the AWS CDK. You can use the resources declared in this demo application as a starting point to mix and adapt to your own architectures later, which should save you quite some time.
Serverless Case Study - Coca-Cola
A while back I talked about how big companies have started using serverless in production and how this is a clear sign that we will see more implementation of the serverless infrastructure in the near future. I’d like to take some time today and talk about one of the companies that are using serverless in production: Coca-cola.
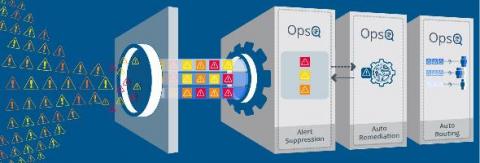
The Real Savings from Intelligent Alert Management
Alert noise is reaching an all-time high in IT organizations. The volume of these alerts from disparate tools and technologies has reached a point where they are greatly undermining the ability of IT organizations to properly manage, secure and optimize services and applications for users and customers. DEJ’s recent study on AIOps found that organizations currently spend $1.27 million annually on avoidable incident escalations that result from non-contextual and non-actionable alerts.