Tales from the ups and downs of running a cloud
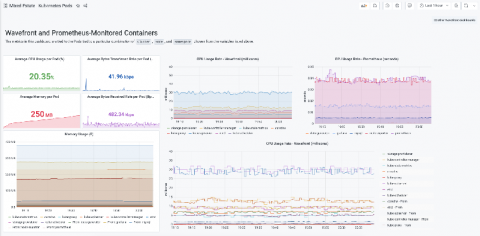
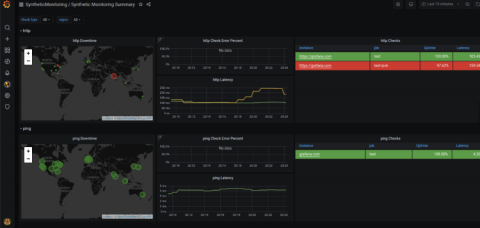
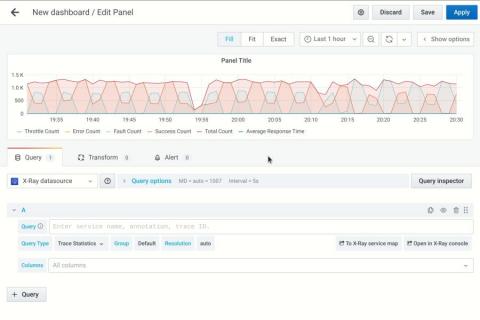
"A long time ago in a data centre far, far away.... Our first episode takes us back to the early days of launching Civo, where we had a fledgling Ceph cluster with a bunch of SSDs in each. Those were darker times, in the early days of OpenStack. As time went by the cluster grew, new bigger nodes were added along with bigger disks.