How Unified Monitoring Can Help Make Your IT Life Easier!
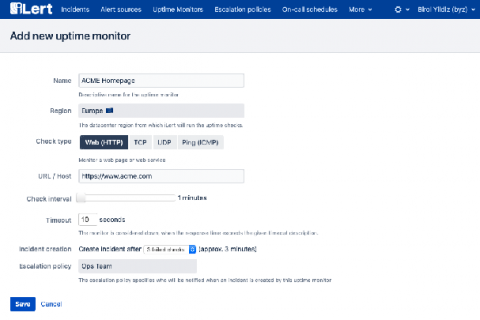
Unified Monitoring provides real-time understanding of what is happening, every time and everywhere on the network, and everything connected to it. With Unified Monitoring, engineers are more able to support proactive identification of root causes and deploy the actions and resources needed to maintain the health and integrity of all connected IT assets.