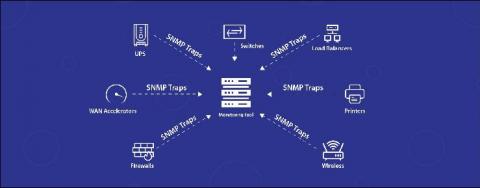
Connecting the dots with Event Correlation
We can’t stress enough on the importance of event correlation in network monitoring. Our customers love correlation! For the love of event correlation we’ve published a blog on why modern organizations rely on event correlation. This is the second blog from the correlation series. You might want to read our previous blog before reading this one.