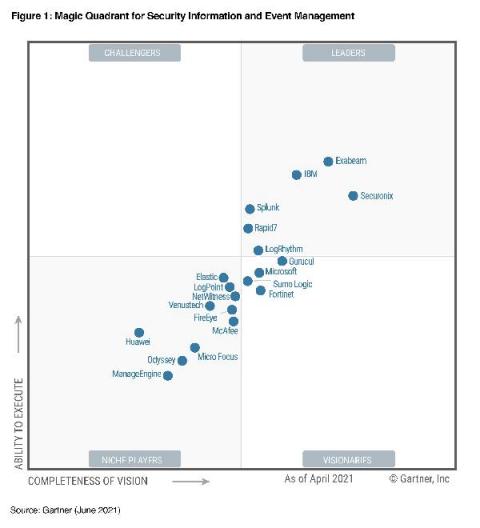
Calico Enterprise: Leverage multiple benefits from the new eBPF data plane
Calico was designed from the ground up with a pluggable data plane architecture. The Enterprise 3.6 release introduces an exciting new eBPF (extended Berkeley Packet Filter) data plane that provides multiple benefits to users.