Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
SOC 1 or SOC 2, which should you comply with and why?
Organizations today are more vulnerable than ever to cyberattacks and data breaches. Whether the attack is executed by an external actor or an insider, the unauthorized intrusion comes at a great cost. This cost may differ, depending on several factors. These include the cause of the breach, the actions taken to remediate the incident, whether there is a history of data infringements, what data was compromised, and how the organization aligned with the authorities and regulators.
How to detect EC2 Serial Console enabled
Recently, Amazon AWS introduced the new feature EC2 Serial Console for instances using Nitro System. It provides a simple and secure way to perform troubleshooting by establishing a connection to the serial port of an instance. Even though this feature is useful in case of break glass situations, from a security perspective, it could be used by adversaries to gain access through an unguarded secondary entrance.
What's new in Sysdig - April 2021
Welcome to another monthly update on what’s new from Sysdig. Ramadan Kareem to all observing the holy month of Ramadan. Our team continues to work hard to bring great new features to all of our customers, automatically and for free! This last month was a big month for security with our release of Cloud Security Posture Management (CSPM), and we had lots of fun designing and releasing our new Cloud Chaos game!
The Global Pandemic Has Led to Unprecedented QR Code Security Challenges
Over the past year, we have witnessed remarkable changes brought on by our response to a global pandemic. Along with accelerated digital transformation and the consumerization of technology, Covid-19 has birthed the everywhere workplace, where users work with any device, to connect to business-critical systems and applications. Work has become something you do rather than a place you go.
How attackers abuse Access Token Manipulation (ATT&CK T1134)
In our previous blog post on Windows access tokens for security practitioners, we covered: Having covered some of the key concepts in Windows security, we will now build on this knowledge and start to look at how attackers can abuse legitimate Windows functionality to move laterally and compromise Active Directory domains. This blog has deliberately attempted to abstract away the workings of specific Windows network authentication protocols (e.g., NTLM and Kerberos) where possible.
Elevate Your Cloud Security Posture with Splunk and Google Cloud
It’s more critical than ever to secure your company data and protect your workloads in the cloud. This blog post is a roundup of the latest technical resources and product capabilities by both Google Cloud and Splunk to enhance your threat prevention, detection, and response techniques, regardless of where you are in your business-transforming cloud journey.
Dashbird becomes SOC 2 compliant
We are pleased to announce that as of 13th April 2021, Dashbird has successfully completed its SOC 2 Type 2 audit. SOC 2 engagements are based on the AICPA’s Trust Service Criteria. SOC 2 audit reports focus on a Service Organization’s non-financial reporting controls as they relate to the Security of a system. The audit was conducted by Dansa D’Arata Soucia LLP.
Thoughts On the Codecov Breach
It was revealed just a few days ago that US Federal investigators are looking into an intrusion and insertion of malicious code into Codecov. As many readers here will already know, Codecov is a software auditing tool that analyses your source code to check for the amount of test coverage. The intrusion targeted the Codecov bash uploader, which is a script that provides a way to send coverage reports to Codecov.
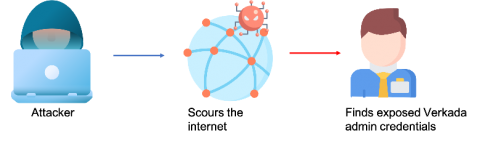
Operation panopticon: How a weak IAM strategy led to the security camera hack across organizations
On March 9, 2021, Verkada, a software company that specializes in making security cameras for monitoring physical access control, was subject to a security hack. Hackers gained access to the video feed of at least 15 thousand cameras deployed across various locations and exposed the inner workings of hospitals, clinics, and mental health institutions; banks; police departments; prisons; schools; and companies like Tesla and Cloudflare.