Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
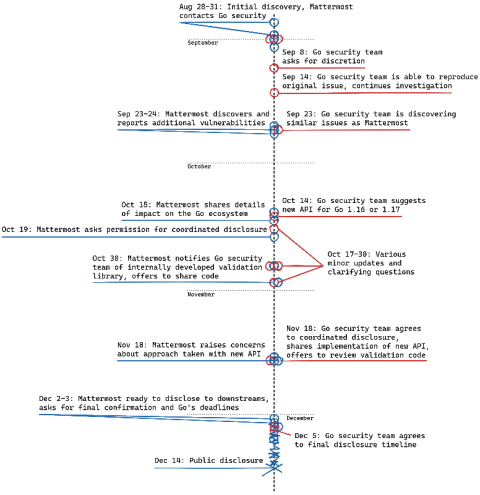
Coordinated disclosure of XML round-trip vulnerabilities in Go's standard library
This blog post is a part of Mattermost’s public disclosure of three serious vulnerabilities in Go’s encoding/xml related to tokenization round-trips. The public disclosure comes as a result of several months of work, including collaborating with the Go security team since August 2020 and with affected downstream project maintainers since earlier this month.
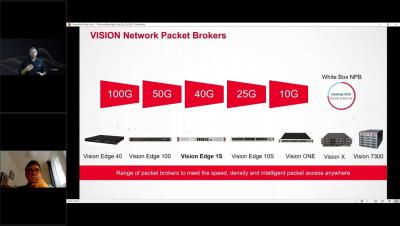
Securing Your Expanding Network Perimeter
Netreo Platform Security
Now, more than ever, Information Security is a topic that should not be taken lightly. All organizations are vulnerable through technology and it is imperative that risk is managed on a daily basis. Netreo realizes the only way to safeguard against threats is to take a holistic approach to managing our technology, people, and processes.
Using Splunk to Detect Sunburst Backdoor
TL;DR: This blog contains some immediate guidance on using Splunk Core and Splunk Enterprise Security to protect (and detect activity on) your network from the Sunburst Backdoor malware delivered via SolarWinds Orion software. Splunk’s threat research team will release more guidance in the coming week. Also please note that you may see some malicious network activity but it may not mean your network is compromised. As always review carefully.
How a mobile device management solution can help with securing devices in the digital workspace
The past decade has witnessed many organizations adapting to a digital workspace, replacing the traditional physical offices setups with virtual workplaces encompassing all the technologies that employees require to get their work done. Because of the pandemic, even companies that were once against the concept of a distributed workforce have now been forced to embrace remote work. Though a digital workspace offers a more flexible user experience for employees, it comes with its own set of challenges.
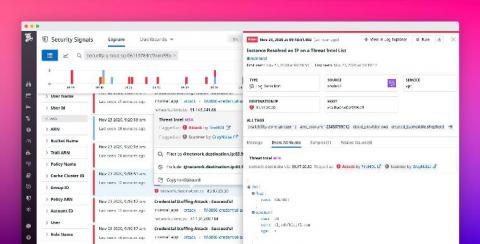
Accelerate security investigations with Datadog Threat Intelligence
Attackers (i.e., threat actors) often reuse techniques or resources, such as IP addresses, hashes, and domains, in multiple attempts to find and exploit vulnerabilities in your systems. Defenders can categorize this data as indicators of compromise (IOCs) and create collections of IOCs in order to look out for potential attacks. These IOC collections are known as threat intelligence.