Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
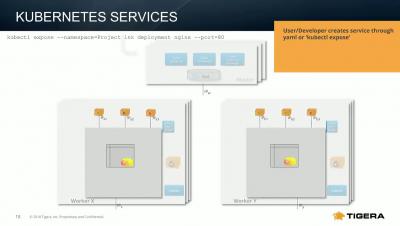
Leveraging Kubernetes Services & DNS
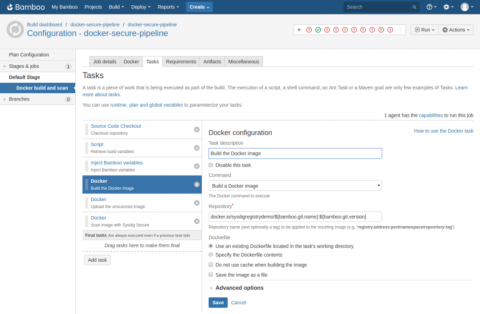
Integrating Sysdig Secure with Atlassian Bamboo CI/CD
In this blog post we are going to cover how to perform Docker image scanning on Atlassian’s Bamboo CI/CD platform using Sysdig Secure. Container images with security vulnerabilities or not compliant with the security policies that you define within Sysdig Secure will be stopped, breaking the build pipeline before being pushed to your Docker registry.
SecOps Is Getting Real (Time)
Companies migrating to the cloud need to ensure they have a strong security posture and can meet compliance requirements. Along with ensuring compliance, companies also are faced with the challenge of tying together multiple security tools that generate a high volume of event data across disparate interfaces and platforms. To help address this challenge, a new security service was introduced at AWS re:Invent 2018: AWS Security Hub.
Conquer it with correlation-Part 3: Cryptojacking
In the previous posts of this blog series, we discussed advanced persistent threats and data breaches, highlighting the importance of data security in today’s times. In the final post of this series, we’ll talk about cryptojacking, a type of attack that can severely affect your network’s integrity, and how you can combat it with event correlation.
Meeting Compliance Regulations with SIEM and Logging
SIEM and log management provide security to your organization; these tools allow your security analysts to track events such as potential and successful breaches of your system and react accordingly. Usually, it doesn’t matter how you ensure your organizational safety-as long as you do.
A Quick Guide to Encrypted Messaging
With it now being so easy to share information, we have a tendency to over-divulge. We check into public places online, tell the world when we’re going on holiday and where, and send and receive risqué photos. However, when it became public knowledge that the NSA, internet service providers, and trusted social media platforms were able to monitor our private messages, the choice to share or not to share was taken away from us.
Hacking custom variables for additional augments in CFEngine
CFEngine 3.12.0 introduced the augments key to the Augments file format. If you are not already familiar with Augments, check it out. It’s a very easy way to define classes and variables very early during agent execution, before policy.
Detecting Data Breaches Fast
Understanding the Impact of the Kubernetes Security Flaw and Why DevSecOps is the Answer
It finally happened. At the start of DockerCon Europe and a week before KubeCon was set to take place in the U.S., researchers discovered the first major vulnerability within Kubernetes, the popular cloud container orchestration system.