Introduction To The Graylog Extended Log Format (GELF)
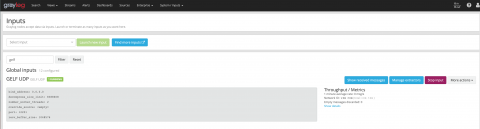
The Graylog ExtendedLog Format (GELF) is a uniquely convenient log format created to deal with allthe shortcomings of classic plain Syslog. This enterprise feature allows you tocollect structured events from anywhere, and then compress and chunk them inthe blink of an eye.