Operations | Monitoring | ITSM | DevOps | Cloud
%term
C# Logging best practices in 2019 with examples and tools
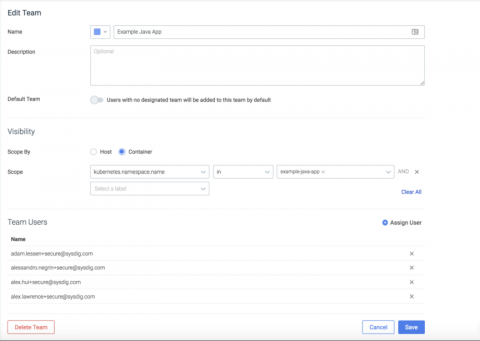
Service based access control with Sysdig Secure Teams
While you’re likely familiar with role-based access control, Sysdig teams introduce the concept of service-based access control. With service-based access control, administrators can define groups of users that have access to policy events, policy configuration, and scanning data limited to a service or set of services, as defined by your orchestration system (think Kubernetes, Mesos, and the like).
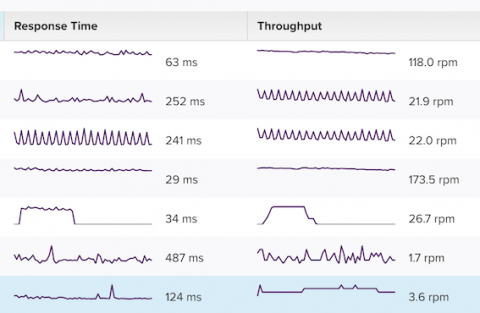
Quick blog post about throughput sparkline feature
We've had sparkline charts of response time for a long time on our Endpoints tab, and now have extended them to the throughput column as well. Quickly isolate endpoints that are spiking with traffic, and drill down into them to diagnose. No need to hunt to see what's causing an unusual trend in traffic.
New Relic Vs Appdynamics Vs Dynatrace
We’ll look at 3 popular APM tools: New Relic, Appdynamics and Dynatrace to see where their strengths and weaknesses lie, how they can help you improve, and how they compare to one another.
Serverless360 v2.0 Product Walk-through
Mattermost 5.5.1 released
Mattermost dot release 5.5.1 for Team Edition (TE) and Enterprise Edition (EE) is now available for download. If your deployment is affected by issues this dot release fixes, upgrading is recommended. Otherwise, you can upgrade to the next monthly release which also includes these fixes.
Answer to the Ultimate Question of (On-Call) Life, the Universe, and Everything: 71
In The Hitchhiker’s Guide to the Galaxy, a group of scientist mice built a mega-computer named “Deep Thought” to Answer “The Ultimate Question of Life, the Universe, and Everything.” After 7.5 million years, the machine produced “42.” At PagerDuty, we did something similar, except we didn’t have scientist mice or wait 7.5 million years.
New generation of web servers based on HTTP/2 and with TLS by default: " Caddy Web Server".
As we all know, Pandora FMS allows the monitoring of practically any device or application. Let’s talk about web content servers. Even the very popular applications or “apps”, made for the Android operating system of our phones, generally use API commands, which are also hosted on web servers to take advantage of the secure protocol (HTTPS).
Spooky Tales of Testing In Production: A Recap and Lessons Learned
Happy December! Back in October, we cohosted a SPOOKY HALLOWEEN meetup with our pals at LaunchDarkly about testing in production. Here’s a review of the talks we saw!