PagerTree Live Call Routing
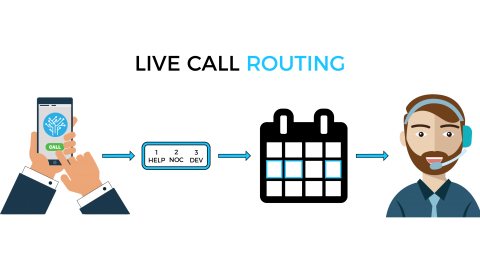
Today, we are excited to announce PagerTree now officially supports Live Call Routing! With Live Call Routing you can route incoming phone calls to the right person using your existing on-call schedules and escalation policies.