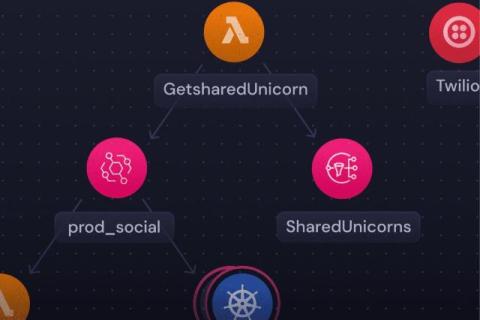
From Siloed IT to Coordinated IT: Navigating the First Steps Towards Autonomic IT
Imagine a world where IT runs itself, monitoring and optimizing technology investments as it runs. Where IT operations are continuous: always available, always responsive, always seamless, always delivering what your organization – and your customers – need. This is Autonomic IT. However, implementing Autonomic IT is not as simple as adding technology and flipping a switch.