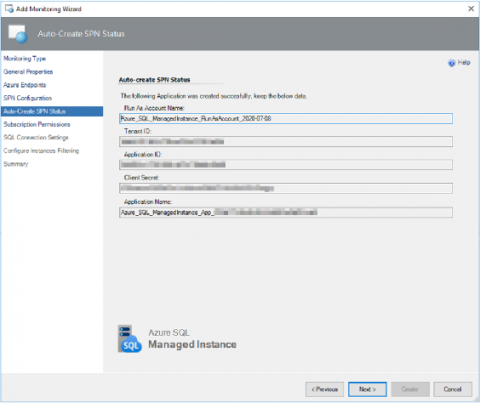
First look at the Azure SQL Managed Instance MP
The Azure SQL Managed Instance is one of Microsoft’s Platform-as-a-Service (PaaS) offerings for SQL. It adds all the features you would expect of a PaaS platform such as automated patching, backups and streamlined high availability whilst closely aligning the technology to on-premises or IaaS workloads to reduce the barrier to entry. The product features near 100% compatibility with the latest Enterprise Edition of SQL Server and the automated Azure Data Migration service.