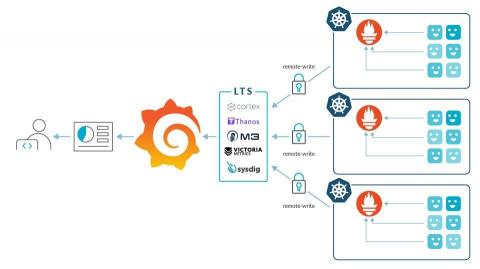
Challenges using Prometheus at scale
This article will cover the most common challenges you might find when trying to use Prometheus at scale. Prometheus is one of the foundations of the cloud-native environment. It has become the de-facto standard for visibility in Kubernetes environments, creating a new category called Prometheus monitoring. The Prometheus journey is usually tied to the Kubernetes journey and the different development stages, from proof of concept to production.