Detecting Data Breaches by Example - Vision Direct
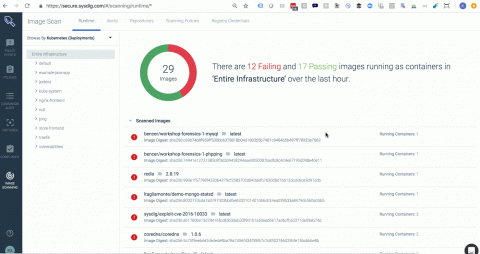
Just as we were getting ready to launch our Data Breach Monitor, we heard the unfortunate news that fellow Yorkshire based business Vision Direct had suffered a malware attack, which resulted in the loss of financial data of around 6,600 customers. So we asked ourselves, could we have detected the same attack using our new monitor? The only way to find out was to infect a website and see what would happen…