How To Cut Down Your Data Usage On Android
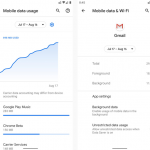
If you’re an Android user, relying on data from your cellular provider is one way of avoiding the risks of free public Wi-Fi – especially if you don’t have the tools or services necessary to give you full protection. Android also has a huge and widely varied user base distributed across the globe. Many of these users operate in regions where free or paid Wi-Fi isn’t even an option. In such instances, going online via cellular data is the only choice they have.