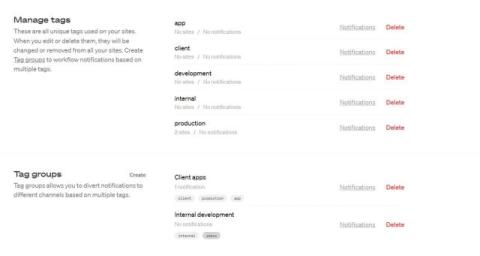
Tag notifications
At Oh Dear, we’re always looking for ways to make web monitoring easier and more efficient for our users. That’s why we’re excited to introduce Tag Notifications, a new feature that expands our notification options beyond site and team-level notifications.