Operations | Monitoring | ITSM | DevOps | Cloud
January 2024
How to Create and Manage a Team in Microsoft Teams
What is a Failover Cluster? How It Works & Applications
How Much Does IT Management Software Cost?
How Much Does Endpoint Management Software Cost?
What is Bash Scripting? Tutorial and Tips
How to Execute a PowerShell Loop: Guide to Boosting Your Scripting Efficiency
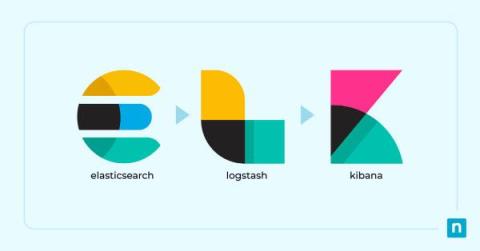
What Is ELK Stack? A Guide to Elasticsearch, Logstash, & Kibana
NinjaOne's 2024 IT Predictions and Trends
4 Ways to Easily Disable Windows Updates in Desktops and Servers
What is a Compliance Audit? Definition & Importance
What is Hyper-V? Key Features and Capabilities
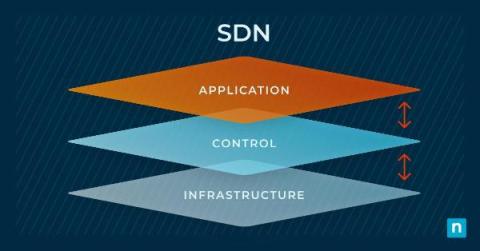
What is Software-Defined Networking (SDN)?
8 Common Network Issues & How to Address Them
Choosing the Best IT Management Solution: NinjaOne vs. Workspace ONE
Establishing effective IT management frameworks hinges on selecting the right solution, vital for optimizing efficiency and safeguarding security. In a recent survey, 72% of small to medium-sized businesses (SMBs) prioritized enhancing security in response to growing cyber threats, with 47% recognizing the importance of automation for operational efficiency in 2024. In this context, two prominent contenders are NinjaOne and VMware’s Workspace ONE.
NinjaOne Named "Best Emerging Vendor" in 2023 Britain's Reseller Choice Awards
We are thrilled to announce that NinjaOne has been named the “Best Emerging Vendor” at the prestigious 2023 Britain’s Reseller Choice Awards. This achievement highlights NinjaOne’s significant impact in the IT sector and its rapidly growing influence within the British market.
How to Set Up a VPN: Complete Guide with Steps
As a growing number of people take note of their online privacy, the Virtual Private Network (VPN) has come to the fore as a simple, accessible way to secure one’s digital footprint. If you’re ready to use a VPN, you may be wondering how to get started. Whether you’re concerned about data breaches, online surveillance, or simply wish to access geo-restricted content, our comprehensive guide is here to demystify the process.
SAML vs. SSO: What's the Difference?
The landscape of modern authentication and authorization in IT systems has evolved significantly over the years. Initially, systems relied on basic password-based mechanisms, which gradually gave way to more sophisticated methods as security demands escalated. The advent of digital certificates and biometric verification marked a significant leap, offering enhanced security.
What Is NIS2?
To better protect its residents, organizations, and institutions, the European Union (EU) has strengthened its stance on cybersecurity with the introduction of NIS2 —the newly upgraded Network and Information Security Directive. This legislative framework is a response to the evolving cyber threats that show no sign of abating. In this article, we demystify NIS2 and share how it’s being used to establish a strong, unified cybersecurity framework across the EU.
Three Reasons Why You Should Learn PowerShell (With PowerShell Training Resources)
PowerShell is an extremely important tool in an IT professional’s arsenal, right next to the rattling box of screwdrivers and pile of vendor swag you got from IT conferences. If you aren’t familiar with PowerShell, let us introduce you! According to Microsoft, PowerShell is a cross-platform task automation solution made up of a command-line shell, a scripting language, and a configuration management framework.
NinjaOne Honored in 2024 BPTW Awards
We are thrilled to announce that NinjaOne has been recognized in the prestigious 2024 Best Places to Work (BPTW) awards program! This accolade is a testament to our commitment to creating an outstanding workplace culture and an environment where innovation thrives.
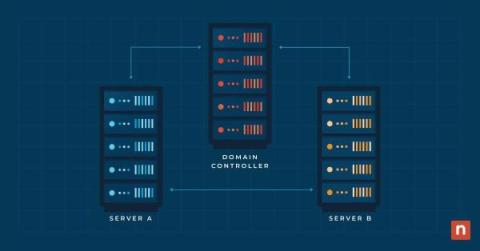
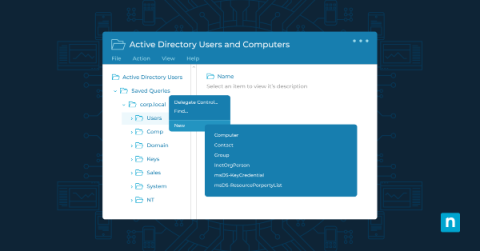
How to Install Active Directory (AD) Users and Computers (ADUC)
Active Directory Users and Computers (ADUC) is a management tool that provides a graphical user interface for managing and organizing the elements of a Windows Active Directory (AD) domain. Key functions include user, group, organizational unit, and computer management, as well as control of security and permissions and trust relationships between domains. ADUC provides system administrators with a centralized interface, simplifying complex tasks and enhancing the security of Windows environments.
How to Start Safe Mode with Windows Command Prompt
Your computer has just decided to throw a digital tantrum, and all the regular troubleshooting tricks just aren’t cutting it. You know that there’s something awry under the hood of your Windows operating system, but navigating the litany of errors is making your head spin. Fortunately, there’s another option: entering Safe Mode via Windows Command Prompt.
3 Ways to Boot Windows in Safe Mode with Networking
We all know the situation: You’re about to start working on your Windows machine, but instead of the familiar welcome chime and desktop, you’re greeted by relentless error messages, unpredictable system behavior, or even the infamous Blue Screen of Death. The good news is there’s a troubleshooter at your disposal. Safe Mode with Networking is the easiest way to troubleshoot issues and get back online quickly. So how can you boot Windows in Safe Mode with Networking?
How to Enable and Disable Kernel-mode Hardware-enforced Stack Protection
As technology evolves, with hackers perpetually sharpening their tools to breach our digital walls, understanding your computer’s built-in defenses is crucial. Kernel-mode hardware-enforced stack protection is one such mechanism. This article will look into the intricacies of this feature, as well as how to enable and disable kernel-mode hardware-enforced stack protection.
How to Remove Trojan Viruses and Prevent Them in the Future
As subtle as they are dangerous, Trojan horses (or just “Trojans”) masquerade as benign software only to unleash havoc once inside your computer. Despite their stealthy nature, there are specific strategies you can employ to safeguard your digital assets from these threats. Below, we’ll discuss how to recognize the signs of a Trojan infection, steps for removing Trojan viruses from your devices, and how to reduce the risk of future infiltrations.
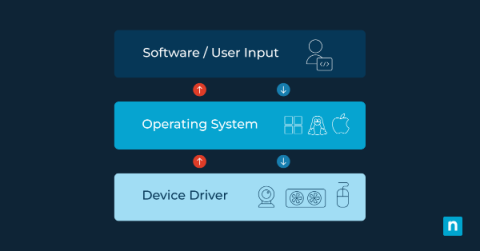
How to Update Drivers on PCs and Troubleshoot Common Issues
You’re in the middle of an important task when suddenly your computer starts acting up—maybe it’s a flickering screen or a printer that’s decided not to heed your commands. Whatever the case, keeping your system drivers updated can help prevent and resolve these problems. But what exactly are drivers, and how do you update them? Below, we’ll offer guidance on how to update drivers on PCs and nip those nagging issues in the bud.
Broadcom VMware Acquisition Impact on Users
The digital world is full of change, so there aren’t many situations that place IT professionals on edge. However, Broadcom’s acquisition of VMware is an exception, since it will impact hundreds of thousands of IT professionals and their organizations. At the moment, VMware has over 500,000 customers worldwide who rely on their services. The Broadcom VMware acquisition, which closed on November 22nd, 2023, has the potential to affect each and every one of these users.
How a Major League Baseball Team Scored Big with NinjaOne's SaaS Solutions
In the high-stakes world of professional sports, IT plays a critical role that goes beyond the field. Recently, a Major League Baseball team demonstrated how switching to NinjaOne for IT management can lead to significant improvements in efficiency, security, and scalability, revolutionizing their operational approach.