Operations | Monitoring | ITSM | DevOps | Cloud
Latest Blogs
Use Case Focused Elasticsearch Online Training Classes to Fit Your Exact Needs
We’ve been working with Elasticsearch since its inception, either with clients on consulting for Elasticsearch products and Elasticsearch production support, or by building our own hosted log management solution. For the last 4 years, we’ve also been sharing our knowledge through Elasticsearch training classes. In 2018, we had remote public training classes on a fixed quarterly schedule, so you can more easily plan your learning time and budget.
Deploying and configuring Datadog with CloudFormation
In this post, we will show you how you can use AWS CloudFormation to automatically deploy infrastructure that is preconfigured to send metrics and logs to Datadog.
Error Monitoring In Zend 3
Zend Framework 3 is a free and open-source PHP framework. It uses a model-view-controller (MVC) pattern which makes its structure consistent and maintainable. It also accesses the database in an object-oriented way. Instead of directly interacting with the database using SQL queries, you can use doctrine object-relational mapping (ORM) to manage the structure and relationships of your data. This makes code easier to write and maintain.
The role of SIEM in PCI DSS compliance
Studies have shown a direct correlation between data breaches and non-compliance. This isn’t to say that compliant companies never get breached, but to reinforce the importance of incident detection and response. Businesses have begun to realize the devastating consequences of data breaches—their finances and reputation are at stake, so many have been taking steps over the last few years to comply with the PCI DSS. The main goal is often an emphasis on achieving continuous compliance.
We've launched an Azure Meetup!
Azure lovers, we have good news for you. Our new years resolution in 2019 is to support the local Azure community. We kicked off with our first Azure Meetup in December. And as the numbers below suggest... people had a great time.
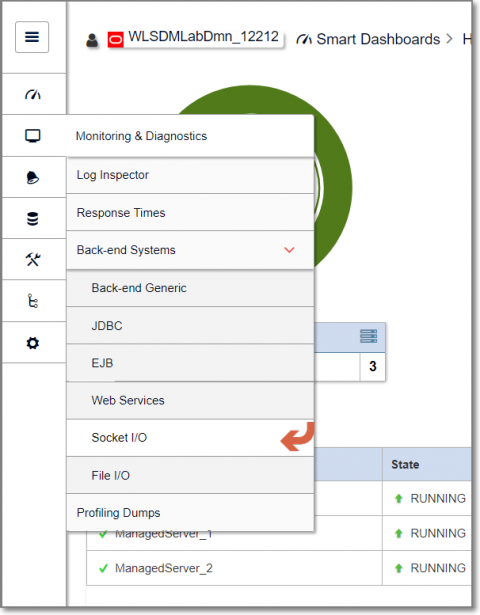
WLSDM: How to monitor Outbound HTTP Socket connection (back-end outbound http/s response times) performance on WebLogic?
In this blog post we prepared monitoring http/s response times performance via WLSDM Back-End system monitoring features. URLs and URLConnections provide a relatively high-level mechanism for accessing resources on the Internet. Sometimes applications are require lower-level network communication, for example, when you want to write a client-server application.
Adding CVE scanning to a CI/CD pipeline
A Docker image contains an application and all its dependencies. As it also contains the numerous binaries and libraries of an OS, it’s important to make sure no vulnerabilities exist in its root filesystem, or at least no critical or major ones. Scanning an image within a CI/CD pipeline can ensure this additional level of security.
Increased Visibility to Manage the New Java Release & Support Model
According to Oracle, Java is a fast, secure and reliable programming language and computing platform first released by Sun Microsystems in 1995. There are lots of applications and websites that will not work unless Java is installed, and more are created every day. From laptops to datacenters, game consoles to scientific supercomputers, cell phones to the Internet, Java is everywhere.
Top 5 DevOps Tools to use before deploying your code
DevOps is an ongoing process requiring constant communication, collaboration, and automation. Teams must be able to move projects from conceptualization to release as quickly and as efficiently as possible. Not only do organizations need to have workflows in place to facilitate DevOps, but they also need the right tools.