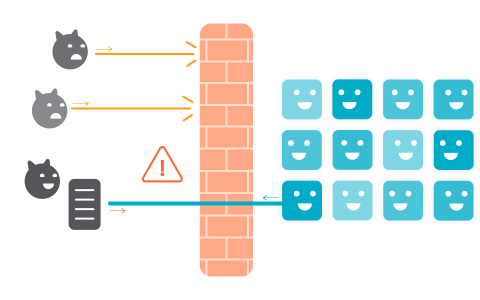
Why Kubernetes is Changing Storage
By 2025, IDC expects worldwide data to grow by 61 percent to 175 zettabytes. This increase in data consumption has contributed to a massive shift within the technology landscape in the last decade, where organizations have been forced to adapt to a digital-dependant world.