Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Complete Guide on Docker Logs [All access methods included]
How Security Engineers Use Observability Pipelines
In data management, numerous roles rely on and regularly use telemetry data. The security engineer is one of these roles. Security engineers are the vigilant sentries, working diligently to identify and address vulnerabilities in the software applications and systems we use and enjoy today. Whether it’s by building an entirely new system or applying current best practices to enhance an existing one, security engineers ensure that your systems and data are always protected.
Guide on Structured Logs [Best Practices included]
How Can the Right Log Aggregator Help Your Enterprise?
The Internet of Things (IoT) revolution has set the beginning of a new age of data transfer. Each day, a massive number of new devices get added to all kinds of network infrastructures, transferring gargantuan amounts of data back and forth. In the next decade, we expect the number of IoTs to grow to a staggering 80 billion connected devices – practically outnumbering the human population tenfold.
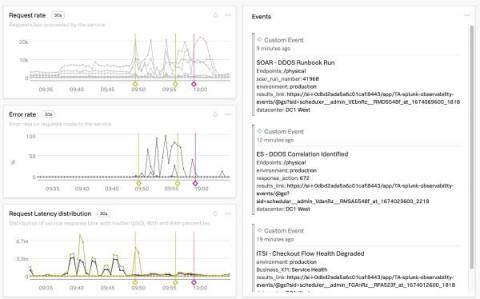
Communicating Context Across Splunk Products With Splunk Observability Events
When an IT or Security issue impacts a development team’s software how are they notified? Is your organization still relying on mass emails that lack context and most engineers have probably already filtered out of their inbox? Communicating between siloed tools and teams can be difficult. How would you like to put IT, Security, legacy processes, and business notifications specific to development teams right into one of their most important tools? Now you can!
A Snapshot of our IT Ops Predictions for 2023
Today executives and customers expect IT and digital services to be available and performant at all times; compromised availability or performance is no longer tolerable. Think about it; when was the last time a digital service was unavailable and it didn’t make the news or social media? When was the last time you visited a website that was unavailable and you waited for the outage to be over, rather than finding an alternative in the moment?
EMEA Predictions for 2023
Yes, it’s that time of year again. As the New Year’s resolutions fade and the planning cycles kick-in, technical leaders in various organisations are often asked to get out the crystal ball to inspire our teams or steer an excited Board.
Root cause log analysis with Elastic Observability and machine learning
With more and more applications moving to the cloud, an increasing amount of telemetry data (logs, metrics, traces) is being collected, which can help improve application performance, operational efficiencies, and business KPIs. However, analyzing this data is extremely tedious and time consuming given the tremendous amounts of data being generated. Traditional methods of alerting and simple pattern matching (visual or simple searching etc) are not sufficient for IT Operations teams and SREs.
Connecting OpenTelemetry to AWS Fargate
OpenTelemetry is an open-source observability framework that provides a vendor-neutral and language-agnostic way to collect and analyze telemetry data. This tutorial will show you how to integrate OpenTelemetry with Amazon AWS Fargate, a container orchestration service that allows you to run and scale containerized applications without managing the underlying infrastructure.