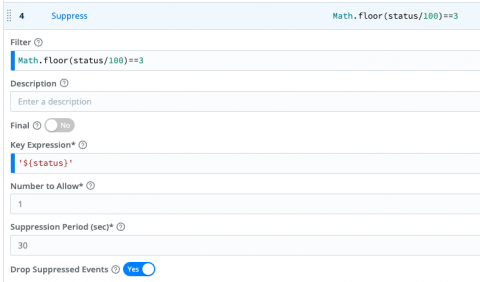
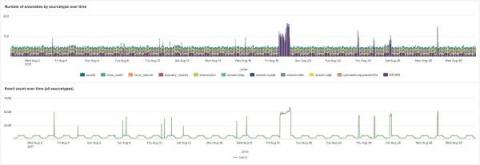
How to correlate logs and metrics with the Linux Node integration for Grafana Cloud
We are pleased to announce that an upgraded version of the Linux Node integration is available in Grafana Cloud, including the capability to visualize logs that are correlated with previously existing metrics. It also includes a new pre-configured dashboard based on the USE method, which focuses on showing resources utilization, saturation, and errors.