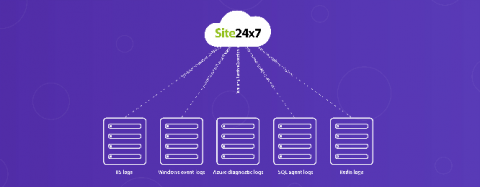
Unlock the Value in Google Cloud with Splunk Observability Solutions
We are excited to announce a strategic partnership with Google Cloud to bring real-time observability into Google Cloud Services and modern applications for our joint customers. Cloud has become essential to modernizing IT environments and enabling the digital initiatives of organizations large and small. Organizations undertake IT modernization – including cloud adoption – to accelerate innovation and increase operational efficiency while optimizing IT spend.