Case Study: How One of the Largest Medical Care Providers in North America Made 200k+ Patients' Happier
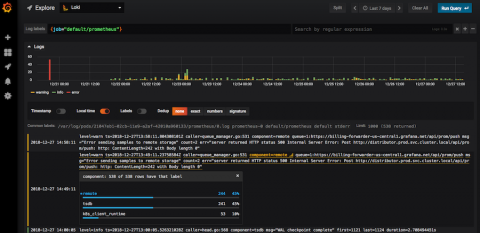
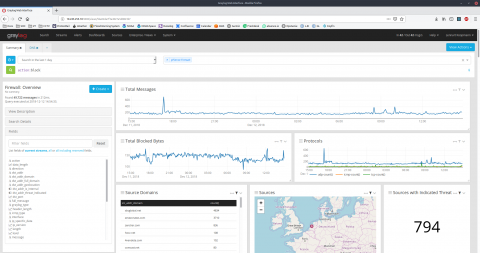
This leading medical care provider manages thousands of facilities and dozens of various patient portals. They needed to find an efficient way to analyze and monitor different services, to obtain maximum availability of their systems – so that patients/doctors get the information they need without interruptions. By implementing XpoLog: Their environment consists of multiple applications, centralized in a main data center, which interacts with all their facilities.