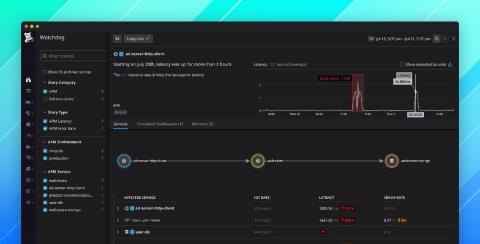
The Internet of Things - Why Cloudsmith Plays a Crucial Role
IoT is slowly, quietly taking over the world. A few years ago, self-ordering fridges, driverless cars, and fully automated homes seemed like the stuff of dreams. And while the technology exists, rollout and adoption is slower than anticipated, amidst security and privacy concerns. That said, IoT is the future, and growth is steady, as the challenges of building and maintaining hundreds of thousands of devices per vendor are getting solved.