Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Captains Log: How we are leveraging CEL for Signals
As engineers, we didn't want to make Signals only a replacement for what the existing incumbents do today. We've had our own gripes for years about the information architecture many old companies still force you to implement today. You should be able to send us any signal from any data source and create an alert based on some conditions. We're no strangers to building features that include conditional logic, but we upped the ante when it came to Signals.
What is tool consolidation - and how can AIOps optimize it?
Tool consolidation is the process of analyzing which IT observability and monitoring tools to use, which to add, and which to retire. By carefully determining the usage and value of your current observability stack, your ITOps teams can consolidate redundant tools and those providing little value to reduce your operational costs. While the benefits of tool consolidation are clear, doing so is anything but.
Tame observability complexity: Understanding the observability tool landscape
Choosing, deploying, maintaining, and rationalizing observability and monitoring tools can be a constant challenge for ITOps, DevOps, and SRE teams. As teams monitor increasingly complex systems, the need for instrumentation that monitors those systems grows at the same rate, leading directly to a growing problem of observability data engineering, integration, and enrichment.
New Features: AI-assisted postmortems, ilert Terraform updates, and expanded ChatOps capabilities
In incident management, staying ahead of the curve is crucial, and that's what we're doing with our latest suite of features designed to streamline your workflow and enhance your response capabilities. Furthermore, you have provided numerous excellent suggestions during this period. We value your feedback and invite you to reach out to us at support@ilert.com to share your experiences with ilert.
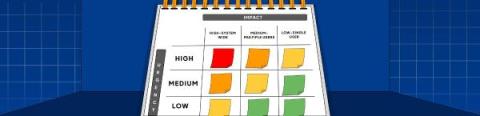
Incident Priority Matrix: A Comprehensive Guide
When multiple users are affected by an incident, it can quickly escalate into a chaotic situation. To effectively manage and prioritize such incidents, organizations need a robust incident priority matrix. An incident priority matrix is a tool organizations use to deal with critical issues quickly. It’s a roadmap for handling incidents efficiently.
Unleash the potential of intelligent, context-aware automation with BigPanda and Ansible
Many ITOps organizations we speak with want a state of self-healing systems capable of identifying and resolving issues without human intervention. Thanks to the progress in AI and ML, AIOps has made significant advancements in areas that automate many of the steps involved with identifying and triaging incidents. We ask ITOps leaders why they aren’t taking the next step with auto-remediating incident response workflows.
What is Vulnerability Management?
Vulnerability management is a critical aspect of a cybersecurity strategy. It refers to the systematic and ongoing process of identifying, classifying, prioritizing, and addressing security vulnerabilities in a network environment. This proactive approach to network security aims to minimize the risk of exploitation by attackers. Vulnerability management is about staying one step ahead of potential threats.
New Study Finds 93% of People Prefer Speaking with a Human Rather than a Chatbot
PagerDuty’s 2023 Holiday Shopping Report: Online shopping will be about the same as last year — top frustrations include poor digital experiences, security, shipping, and tracking issues.